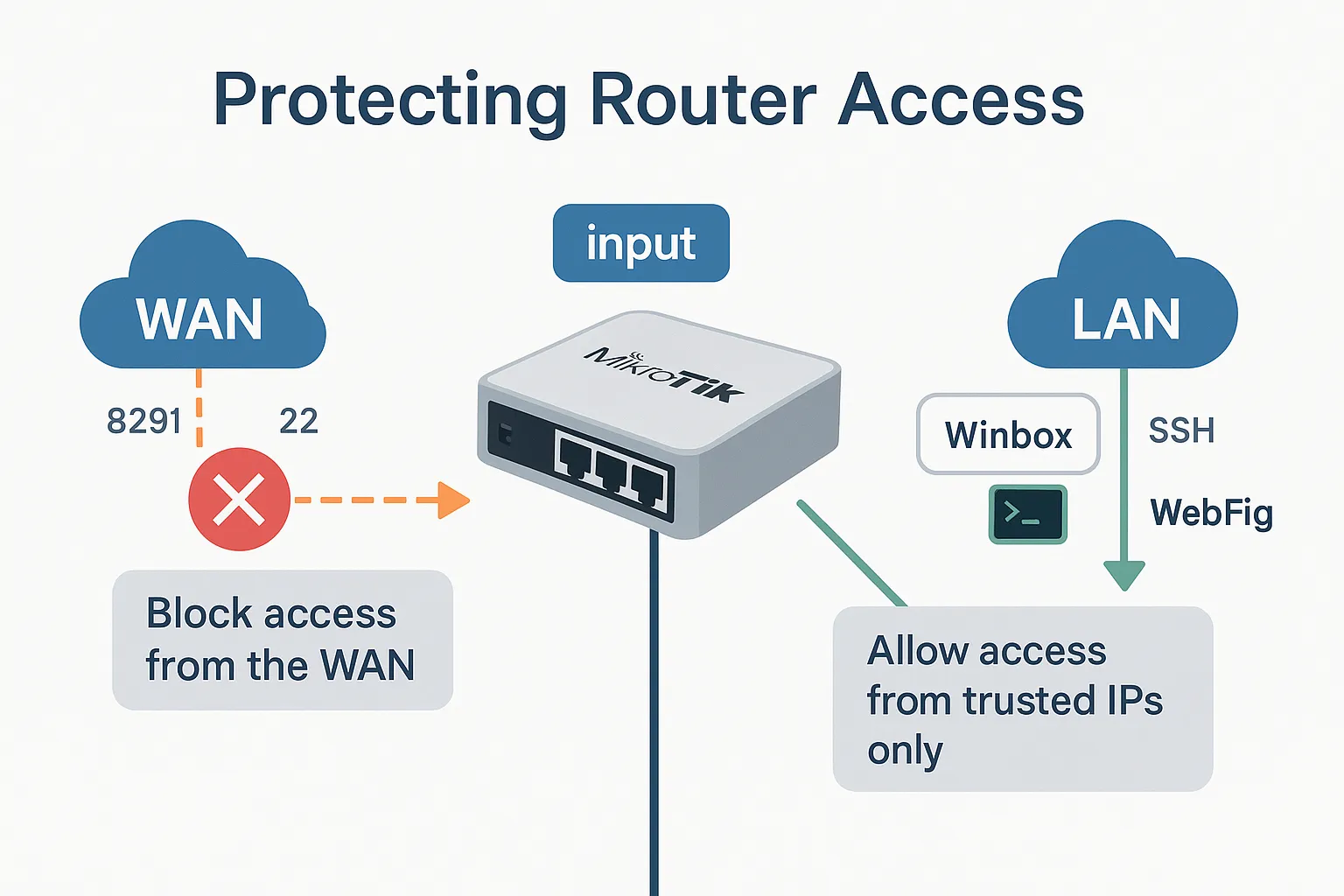
Why This Is Critical
The input chain governs access to your router itself — the Winbox interface, SSH terminal, web admin panel (WebFig), DNS, and more. If this chain is open, you’re essentially leaving your MikroTik naked on the internet.
And bots will try to log in. Constantly.
Even if they fail, just the traffic volume can cause performance issues, log flooding, and trigger ISP abuse reports.
So, our goal is clear: Block everything by default, then allow only trusted IPs to access administrative services.
🔧 Step-by-Step Strategy
- Allow established and related connections
- Allow access from trusted IPs / LAN
- Block new WAN connections
- Log attempts from unknown sources (optional)
- Disable unused services like FTP, Telnet
- Secure access with strong passwords and timeouts
🔐 Step 1: Allow Safe Traffic
First, as discussed in earlier sections, allow already-established connections and those related to them (like ICMP replies):
/ip firewall filter
add chain=input connection-state=established,related action=accept comment="Allow established & related"
This ensures existing connections, like your current Winbox session, won’t get cut off.
👥 Step 2: Allow Access from Trusted Sources
Here, we’ll permit only specific IPs and subnets — defined earlier in our TRUSTED_IPS and LAN_SUBNETS address lists.
/ip firewall filter
add chain=input src-address-list=TRUSTED_IPS action=accept comment="Allow admin access from trusted IPs"
/ip firewall filter
add chain=input src-address-list=LAN_SUBNETS action=accept comment="Allow access from LAN"
You can also target specific ports:
add chain=input src-address-list=TRUSTED_IPS protocol=tcp dst-port=8291,22 action=accept comment="Allow Winbox & SSH"
❌ Step 3: Drop Everything Else
Now it’s time to block everything not explicitly allowed. And we’ll do this carefully, placing this rule after all previous accepts:
/ip firewall filter
add chain=input connection-state=new action=drop comment="Drop all new inbound connections"
This rule will reject any new connection attempt to the router itself — unless it came from a trusted address.
🔔 Step 4: Optional Logging (for Curiosity or Forensics)
Want to see who’s knocking on your WAN interface? You can log their attempts like this:
/ip firewall filter
add chain=input connection-state=new log=yes log-prefix="Blocked INPUT: " action=drop
But be careful — under attack, logs can grow rapidly. Use it temporarily or with rate limits.
🛠️ Step 5: Disable Unused MikroTik Services
By default, RouterOS enables things like:
- Telnet (TCP 23)
- FTP (TCP 21)
- WebFig (TCP 80, 443)
- Winbox (TCP 8291)
- SSH (TCP 22)
- API ports (8728, 8729)
If you’re not using a service — disable it:
/ip service disable telnet
/ip service disable ftp
/ip service disable www
/ip service disable www-ssl
You can also restrict services to certain interfaces or address lists:
/ip service set winbox address=192.168.88.0/24
🔒 Step 6: Secure Credentials and Access Settings
Even with firewall rules, don’t forget:
- Use strong passwords for all user accounts
- Don’t use the default
adminuser — disable or rename it - Set
System → Users → Group → Policiescarefully - Set Winbox inactivity timeouts under
Tools → Settings
✅ Summary
✔ You’ve locked down direct access to the router
✔ Only trusted IPs or LAN can manage the router
✔ Everything else is blocked or logged
✔ You’ve disabled services you don’t use
✔ Your firewall input chain is clean, simple, and secure