Introduction: The Golden Rule of Data There’s an old saying in IT: «If your data doesn’t exist in three places, it doesn’t exist at all.» In a virtualized […]
Popular Posts
Recent Posts
Configuring Proxmox Networking: Bridges, VLANs, and Bonds Explained
Introduction: The Heart of Your Virtualized World Once you have Proxmox installed, you’ll quickly realize that networking is the backbone of your entire virtualization setup. It’s how your […]
How to Install Proxmox VE 8: A Beginner’s Step-by-Step Guide
Introduction So, you’ve decided to build your own powerful server with Proxmox VE? Excellent choice! You’re on your way to creating an amazing homelab or small business environment. […]
The Ultimate Guide to Proxmox VE in 2025: From Zero to a Fully Functional Homelab
Introduction: What is Proxmox VE and Why Does it Dominate in 2025? Welcome to the definitive guide to Proxmox Virtual Environment (VE). In the ever-evolving world of IT, […]
Deploy Proxmox VMs with Terraform in a Docker Container
Automating your infrastructure is a cornerstone of modern DevOps, and Proxmox is a fantastic virtualization platform. When you combine it with Terraform, you unlock the power of Infrastructure […]
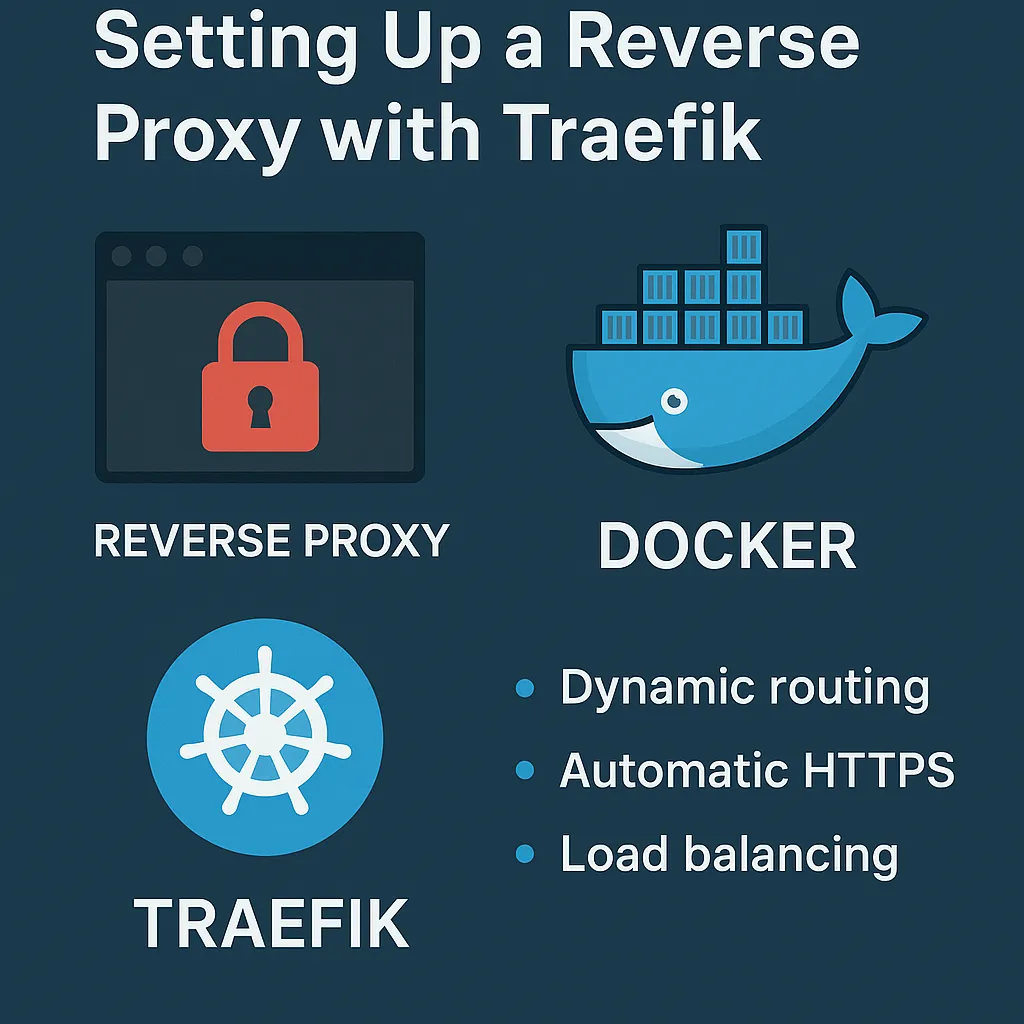
Ultimate Guide: Setting Up Traefik as a Reverse Proxy in Docker (with Let’s Encrypt, Cloudflare, and Secure Services)
Introduction: Why a Reverse Proxy? In modern self-hosted environments, you’re often running multiple services — like a photo gallery (e.g., Immich), media server (e.g., Jellyfin), and dashboards. If […]
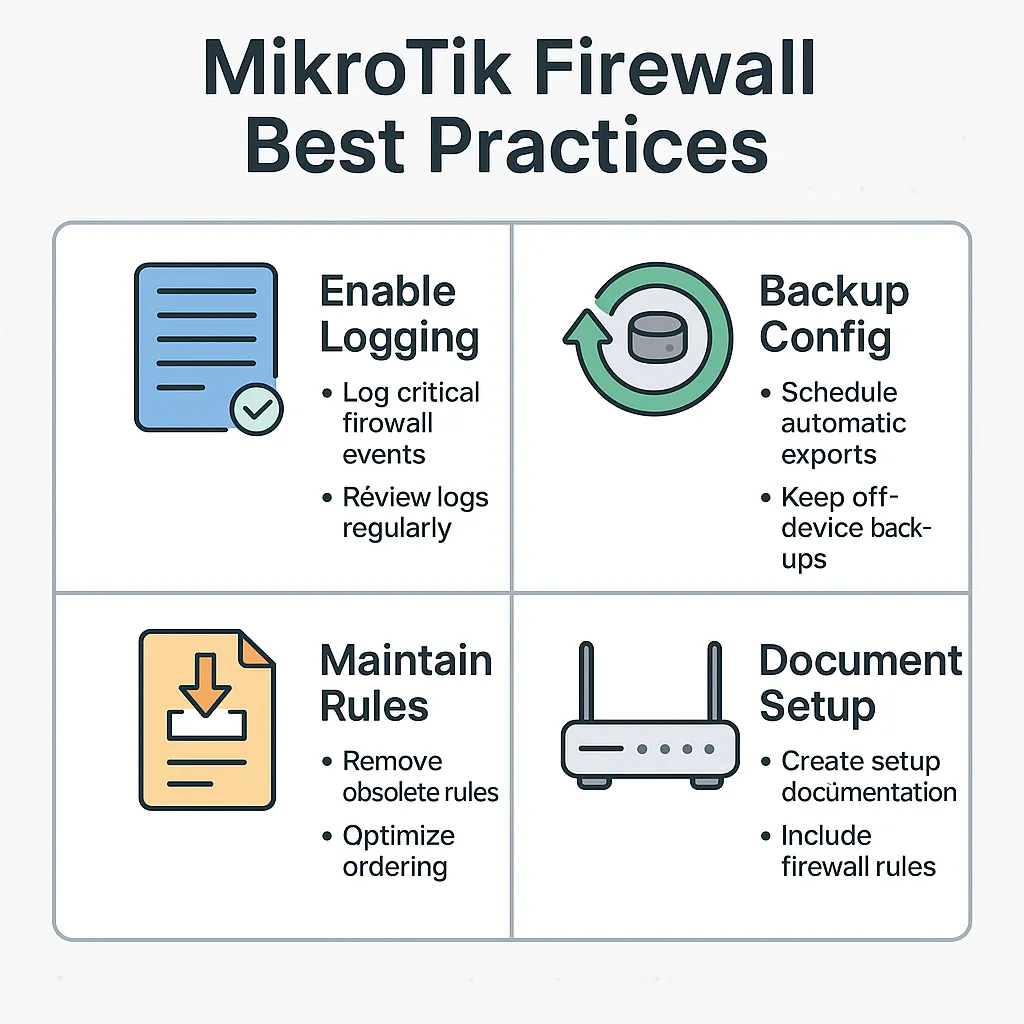
Firewall Logging, Backups & Best Practices
— Keep It Clean, Recoverable, and Easy to Maintain Why This Matters A solid firewall config can take hours to build — but minutes to lose. Whether it’s: […]
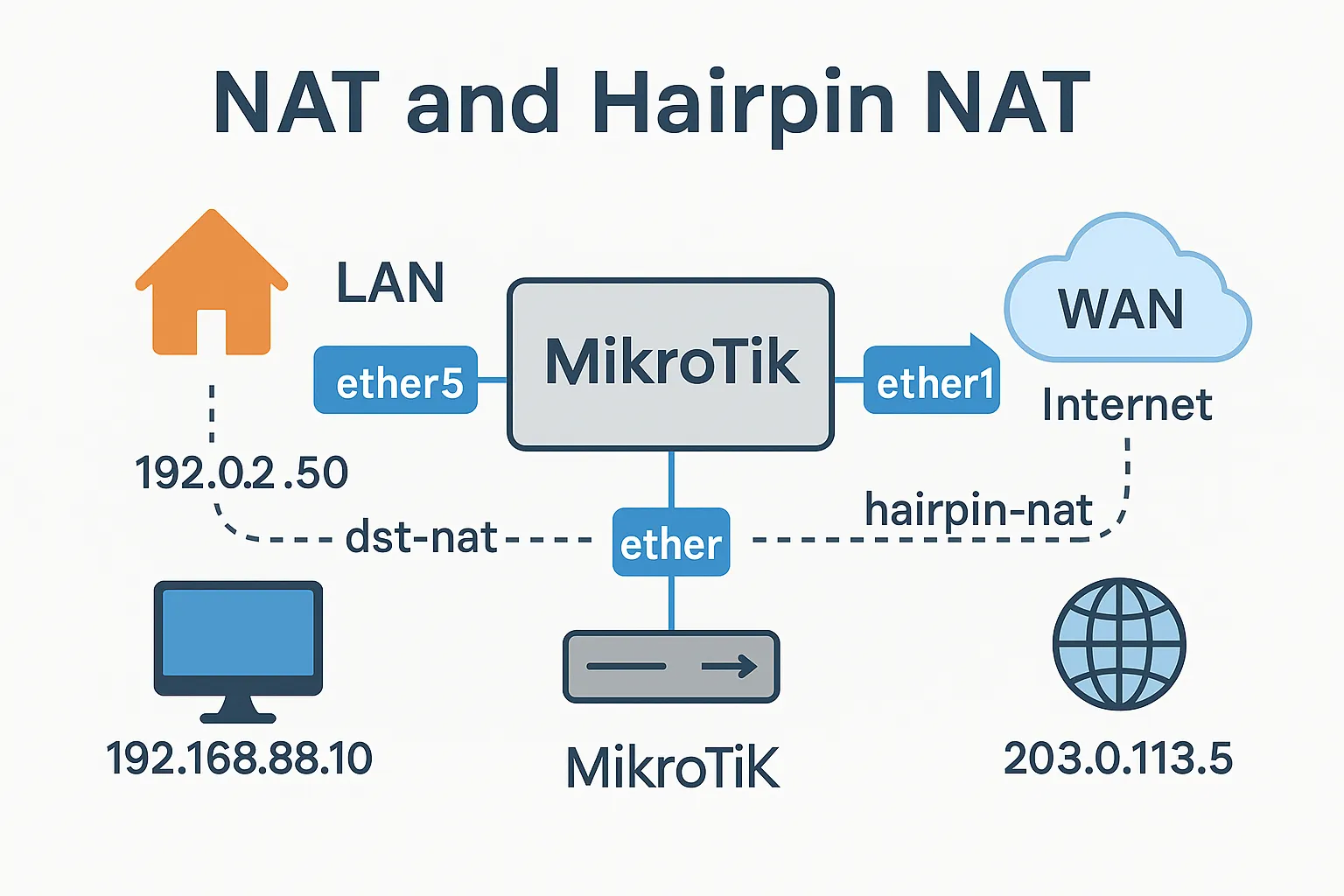
Understanding NAT & Hairpin NAT in MikroTik
— Make Local and External Access Work Seamlessly What is NAT? NAT (Network Address Translation) lets multiple devices on your internal network (usually private IPs like 192.168.x.x) share […]
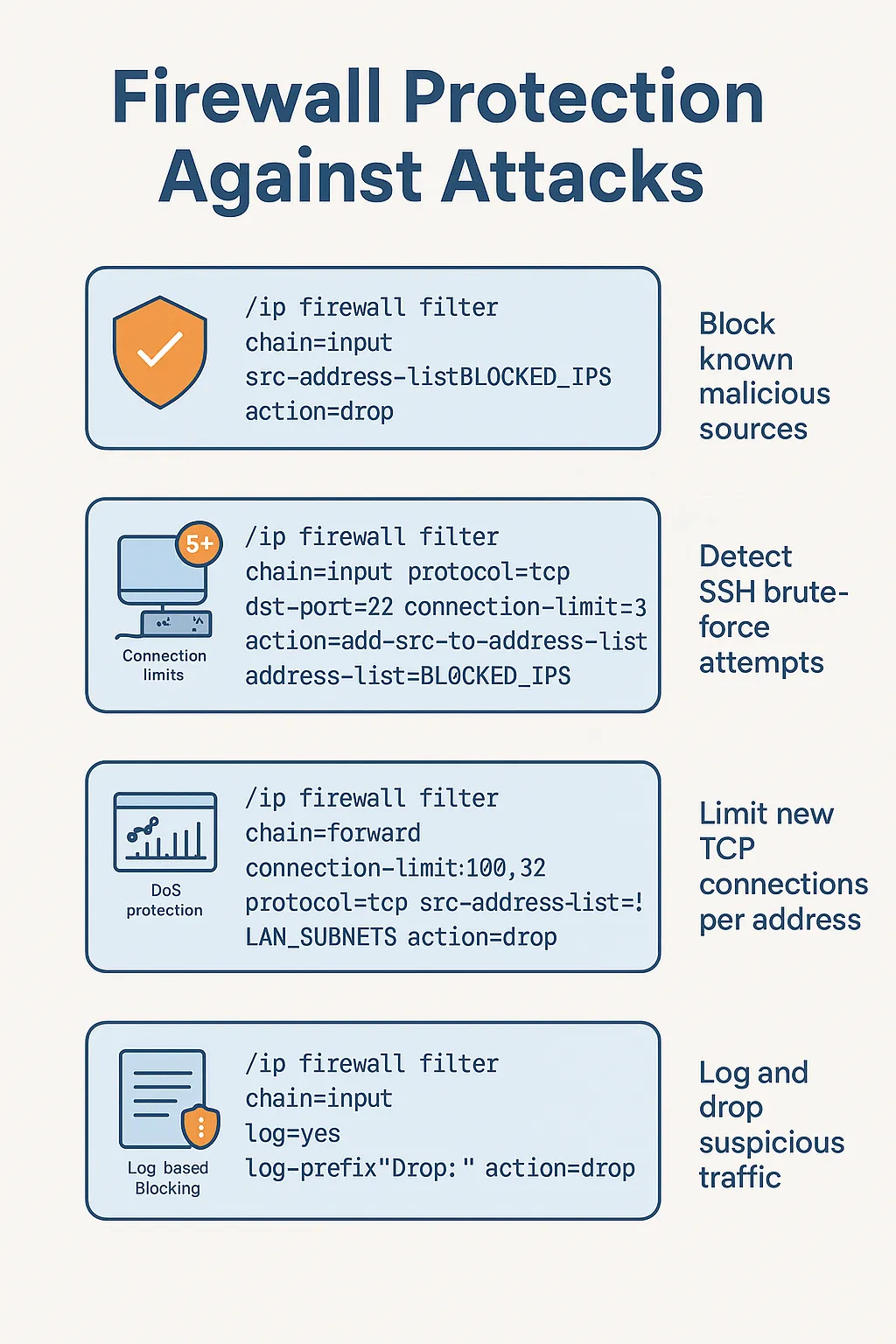
Firewall Protection Against Attacks
— Block, Detect, and Log Like a Pro Why MikroTik Routers Get Targeted If your router has a public IP — it will be scanned.Thousands of bots around […]
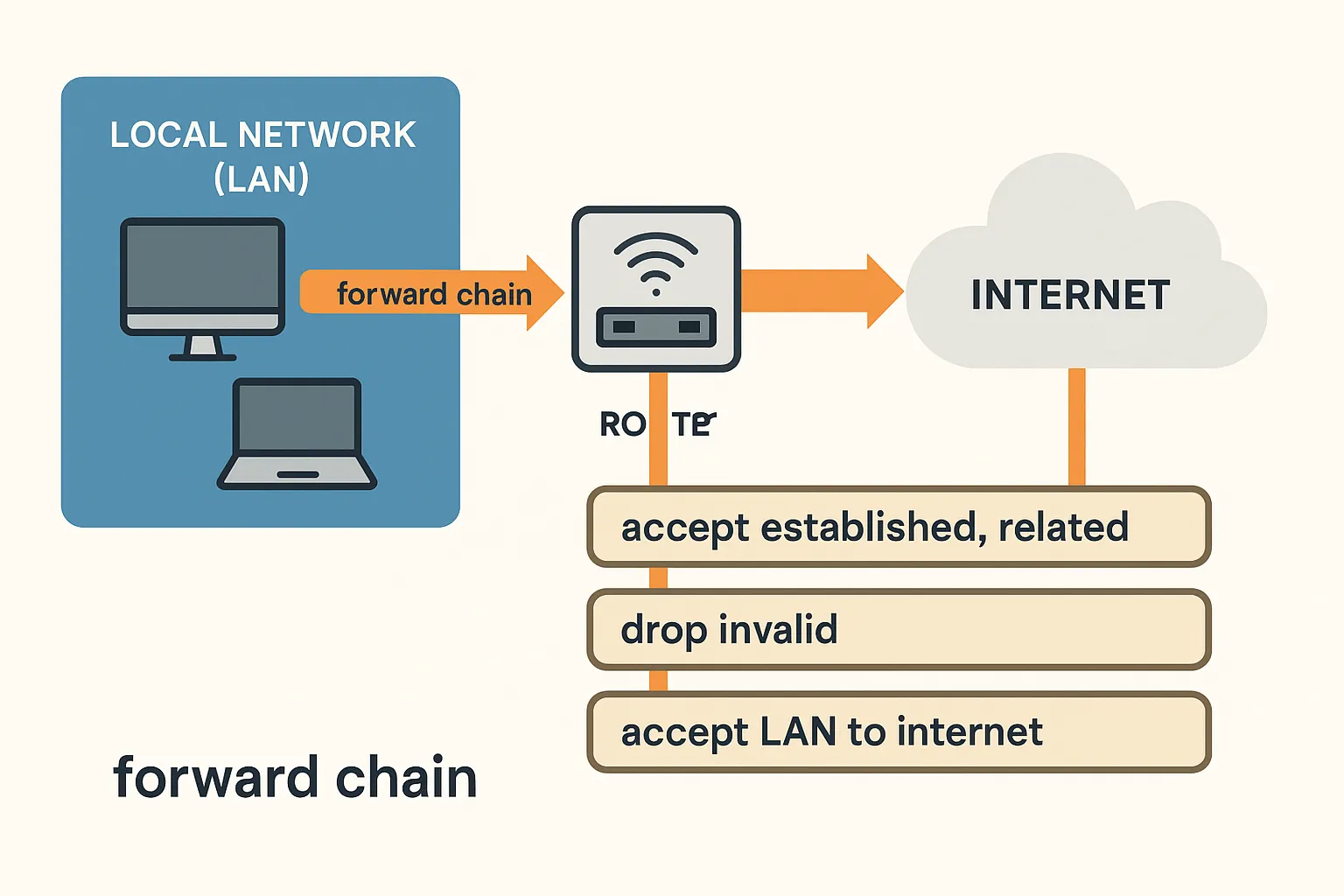
Forward Chain Firewall Rules: Controlling LAN, Guests, and the Internet
What Is the Forward Chain? In MikroTik’s firewall, the forward chain handles traffic that passes through the router — not destined to it. Examples: If it goes through […]